Several months ago, there was a call for essays on how the National Security Act (originally in 1947) look like now. I submitted my essay, but it did not get to the finalist stack, but I knew I was competing with a ton of people that write essays for a living, so I did not have any expectations. Well, I thought that I would put it in my blog to let readers see it and make their own decision. Any comments on it would be considered and appreciated. Thank you.
BACKGROUND
The National Security Act of 1947 performed myriad adaptations to how the United States acted militarily on the world stage in both an offensive and defensive capability. First, and probably the one area that needs reiteration when addressing the National Security Act of 1947 was the creation of the United States Air Force. Quickly reviewing where the United States was in 1947 is critical to understanding why this creation was vital.
The United States had just made a major contribution to the defeat of Germany in the East and Japan in the West, putting a finish to World War II with the help of allies. In both situations, it was very evident that the Atlantic and Pacific Oceans were no longer natural barriers to invaders. From experience, a strong Air Force would provide a dual purpose: (1) To provide intercontinental offensive and defensive capabilities, and (2) provide the medium to carry the new nuclear weapons. It is important to add that the United States was the ONLY country in the world that possessed (and used) nuclear weapons in a combat situation.
The National Security Act of 1947 also created a group of organizations that could keep tabs on our foreign enemies to keep them in check: the Central Intelligence Agency and the National Security Agency among them. Remember that the Soviet Union, an ally during World War II (although more of a “frenemy” than friend), became a major foreign adversary after the War. They not only maintained their hegemony, but made sure that they would have a buffer against any further attempts to invade their country. By occupying East Germany; Poland, Bulgaria, Czechoslovakia, Romania, and other Eastern European became possible (and, in fact, real) future targets of Soviet expansion. The USSR was ensuring an alliance against an impending western alliance, a prophesy that would come in 1949 in the form of the North Atlantic Treaty Organization or NATO. (Editors, 2010).
Besides a post-war Europe, what was the environment like in the US in 1947? The dollar was strong at that time (Webster, 2021), and the US was coming off a victory that made them feel invincible (Library of Congress, n.d.). The US was the only one with a nuclear weapon and their manufacturing was second to none (Pruitt, 2020). Also, and most importantly, they were the only major ally that did not suffer heavy bombing damage (or any for that matter) during the war, so their manufacturing capability was never really decimated like facilities in Europe. In addition to all these advantages, there were NO satellites in space at that time (Sputnik was not until 1957) and the space race was more science fiction than science. From military educational experience, the US established the National Security Act to show the US as a strong, defensible, and loyal ally. It would be able to defend any US ally with strength; enemies of the US should fear their capabilities. This was redoubled in President Kennedy’s inaugural address in 1961 (Kennedy, 1961). The US citizens were well protected and understood that their military was the strongest in the world.
CURRENT EVENTS
The National Security Act of 1947 looked outward to our enemies of which there were few: the Soviet Union and their allies with their strong military and Communist ideology, and Yugoslavia with Marshal Tito in charge of their Communist ideology. Communist China did not exist at that time but was taking hold, with Korea and French Indochina (Vietnam) slowly evolving their ideology thanks to Communist leaders that actually helped the Allies defeat the Japanese. In 2022, the US has a plethora of enemies both internally and externally that would demand the new National Security Act’s attention. First, internal strife caused by activism from both the far left and far right are causing fissures within the very foundation of the United States. These fissures, although relatively slight at the moment, could cause massive chasms within the next decade, even affecting the US military. These weaknesses are no doubt being noted by our enemies, seeing an implosion as much more productive for their ends than any type of external involvement. Some defense analysts have noted these in their current articles (). Second, enemies are not easy to identify in today’s world environment. The former Soviet Union at one time perceived the US as a possible enemy, but others see them as a strong possible ally for peace (Nesterov, 2005). Poland and Czechoslovakia joining NATO put a dent in the buffer of the former Warsaw Pact that helped secure Russia; and Ukraine and Georgia (FSR) are both becoming hot spots because of their resources and their geographic location with regard to oil transport to Russia (Andreas Billmeier, 2004). In 2014, Russia invaded Crimea in order to get a foothold on the only ice-free ports that were being used by both Russia and Western Europe (Chuma, 2016). Taking those now gives Russia the ability to transit the Black Sea into the Mediterranean without having to first send ice breakers ahead. Last, but certainly not least, is the expansive nature of US foreign policy. The US is involved in most continents of the world militarily. It has navies on most oceans, and ground representation with virtually every foreign military. The US Military Schools have foreign military students and the Air Force, Navy, and Army trains foreign military pilots. In essence, the US has made the world a classroom for ideology, military, and economic expansion.
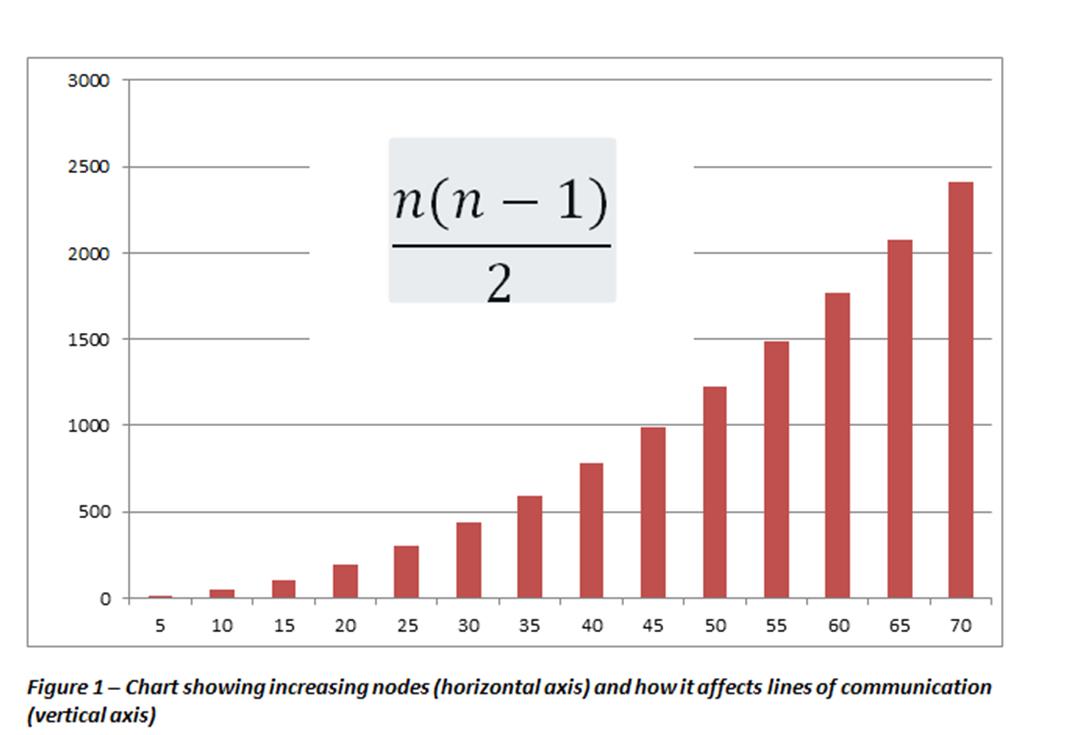
With these ideas as the foundation for 2022, the National Security Act should strengthen the following ideas. First, the National Security Act should make very clear the preamble of the US Constitution (maybe even including it as the first words of the document). The statement “provide for the common defense” means that the US national security is primarily the responsibility of the US citizens, whose representatives in Congress have two main duties according to the Constitution and one being the national defense. It is the US citizen that is responsible for the example set to future citizens. This idea of common defense is something that may not be understood in this era of a well-protected United States. In fact, US military officers and enlisted take an oath before becoming a servicemember. The oath begins with “I swear/affirm that I will support and defend the Constitution of the United States against all enemies foreign and domestic.” As one study showed, there is more of a fear of civil unrest than becoming involved in another world war (Christopher Bader, n.d.). What these examples would indicate is that the National Security Act of 2022 should be focused on the quelling of the fears about domestic threats and secondarily cover those fears that stem from external threats. This would mean an expansion of organizations that are currently enmeshed in both external and internal threats to the National Defense. The Federal Bureau of Investigation (FBI) is responsible for domestic terrorism, but that duty is becoming blurred with the National Security Agency (NSA), who is responsible for foreign terrorism. Since the National Security Act was passed, only a few more organizations have been created in order to fight the continuing transformation of threats (besides the Air Force). Creating Joint Commands helped the various arms of the military come together to combat rogue states and factions. From intelligence experience, part of this creation was a direct result of the failed Iranian Hostage attempt in April 1980. The formation of the Director of National Intelligence (DNI) was a direct result of the September 11 attacks on the United States. Interestingly enough, the Director of Central Intelligence (DCI) was formed from the National Security Act of 1947, and could have been transformed into the DNI, but the DCI is also the Director of the CIA, which could result in some conflicts of interest.
TRAINING
The National Security Act of 2022 should focus on a training agency that will help to inform the Federal and State Agencies about impending and actual threats against the United States. This training agency would be composed of past and present intelligence operators including those that have seen intelligence use in actual combat. This agency would be given carte blanche to ALL Federal and State government agencies’ training curriculum to ensure that they have the appropriate information needed to conduct classes on the prediction and exploitation of adversarial information. The training will be consistent and constant, with updates to current threat information provided much like weather prediction – at least 3 times a day. Every training agency will have access to the overarching training agency and collaboration will be part of the policy.
Why is training so important? According to one source, training is the foundation for combat operations (Greer, 2018). It is the one consistent factor in the success or failure of any operation, military or otherwise. What this means is that all intelligence analysts would be given the same training, regardless of their environment. What the goal of the training should be is to teach critical thinking skills and methods to apply this critical thinking. Along with critical thinking is the ability to think creatively. In The Tao Te Ching, one area of importance was “Forgetting Knowledge” which states, in part, “He who devotes himself to learning [seeks] from day to day to increase [his knowledge]” (Sun Tzu, 2016, p. 222). In essence, the training agency would be the front line of prevention for both internal and external threats to US security.
This is not a new approach. When military failures occur, there is often a revamping of training in order to modernize the military with respect to this failure. In other words, the reason for the training is to not make the same mistake again. The joint venture after the failed Iran Hostage Rescue resulted in a focus on joint operations. The agency can be called the Federal Training Agency (FTA) and have regional offices located in the same cities as Department of Defense has their regional headquarters. The Agency would have positions in the training specialties, but have military and civilian that are part of the operational and intelligence areas. Their jobs would be to train and advise the different Federal Agencies on their training functions. This could help reduce the training functions of the different military services (such as TRADOC for the Army, Education and Training Command for the Air Force, etc.), but it would not be designed to eliminate those functions. The pure function of the Training Agency would be to supplement and advise the different training functions of the Federal Government.
How would this be a value-added measure for National Security? The United States is moving into an unknown time period with regard to National Will and National Power. Much like we teach our teenagers to drive cars, we also need to train our policy makers to understand the world, not just our enemies. The Training Agency would be responsible for providing an historical perspective to international intentions. For example, why does Russia want to conquer Ukraine? Why do the Israelis and Palestinians not get along? Why does China want to become a world power? These are questions that help establish why our National Security exists. It also helps the policy maker and operator understand it may be a difficult challenge to apply certain methods that were previously effective against adversaries that we do not understand.
DATA
Besides training as a method for preparing the national security decision makers, the idea of data standards and data training has been something that the Federal Government has just recently addressed (Council, 2021). It is evident that every military service has their preferred software and data repository and the DoD has attempted to corral this type of issue. However, by having various data methods, it invites adversaries to exploit vulnerabilities. The US has a Cyber Command that has offensive capabilities with its neighboring National Security Agency as the defensive end of the exploitation arena. If there is a Cyber Command, why is there not a Federal Agency that has accountability for all the different data methodology in the US Government? The National Security Act of 2022 should address these data differences and establish a consistent data dictionary that will help the US Government mitigate the vulnerabilities that exist with each agency having their own data definitions, dictionaries, and methodologies. For instance, the Social Security Administration (SSA), and the Centers for Medicare and Medicaid Services (CMS) are less than 2 miles from one another, but each of them has separate departments for data exchange (Social Security Administration) (Centers for Medicare and Medicaid Services). Every medical facility has the same personal data (birth date, Social Security Number, etc.), yet patients are constantly filling out forms with those personal data. The reason is that the data is not available or accessible through a consistent data port.
In addition to helping the Federal Government set data standards, the Federal Database Agency (or whatever it is named) will be partners with the Cyber Command to ensure that the vulnerability of the Federal Data Bases will be mitigated if not remediated using Federal Standards that already exist within the Federal Government.
Will these changes be met with challenges? As a former Federal Government Employee and military officer, every change in government is met with some form of “push back” but in the long run, these changes would be done to pare down Federal Government, cajoling standards rather than forcing it through mandate. From experience, advice and consent is much better than force-feeding the policy.
SUMMARY
In summary, the National Security Act of 2022 will be in sharp contrast to the National Security Act of 1947 in that it will focus internally more than externally. It will consist of both training and data; training the policy makers on the history and consequences of their decision as well as the standardization of data within the Federal Government. In this way, national security decisions will be the foundation of the Act, not just a name. Table 1 shows some of the comparison between these two documents. The world today is not post-World War II. It is time we document that fact.
| National Security Act 1947 | National Security Act 2022 | |
| Focus | External Threats | Internal and External |
| Foundation | Pos-World War II geography and ideology | The US Constitution (We the People…) |
| Main Points | Creation of organizations to counter nuclear threat and adversary forces | To understand the world as it exists and work to counter threats before they occur |
| Organizations | Air Force, Intelligence | Training, Data |
Table 1 – Comparison of National Security Act of 1947 vs National Security Act of 2022
References
Andreas Billmeier, J. D. (2004, November). In the Pipeline: Georgia’s Oil and Gas Transit Revenues. Retrieved from imf.org: https://www.imf.org/external/pubs/ft/wp/2004/wp04209.pdf
Centers for Medicare and Medicaid Services. (n.d.). IRS-SSA-CMS Data Match. Retrieved from cms.gov: https://www.cms.gov/Medicare/Coordination-of-Benefits-and-Recovery/EmployerServices/IRS-SSA-CMS-Data-Match
Christopher Bader, E. D. (n.d.). Chapman University. Retrieved from Wilkinson College: https://www.chapman.edu/wilkinson/research-centers/babbie-center/survey-american-fears.aspx
Chuma, L. J. (2016, December 15). Russia Seeks Ice-Free Ports in Ukraine, Syria. Retrieved from Maritime Executive.com: https://maritime-executive.com/editorials/russia-desires-ice-free-ports-in-ukraine-syria
Council, F. C. (2021). Data Skills Training Program Implementation Toolkit. Retrieved from resources.data.gov: https://resources.data.gov/resources/data_skills_training_program_implementation_toolkit/
Editors, H. (2010, April 14). History. Retrieved from History.com: https://www.history.com/topics/cold-war/formation-of-nato-and-warsaw-pact
Greer, J. (2018, October 4). Training: The Foundation for Success in Combat. Retrieved from heritage.org: https://www.heritage.org/military-strength-topical-essays/2019-essays/training-the-foundation-success-combat
Kennedy, J. F. (1961, January 20). Inaugural Address, January 1961. Retrieved from jfklibrary.org: https://www.jfklibrary.org/archives/other-resources/john-f-kennedy-speeches/inaugural-address-19610120
Library of Congress. (n.d.). US History Prime Source Timeline. Retrieved from Library of Congress: https://www.loc.gov/classroom-materials/united-states-history-primary-source-timeline/post-war-united-states-1945-1968/overview/#:~:text=When%20World%20War%20II%20ended%2C%20the%20United%20States,paled%20in%20comparison%20to%20any%20other%20major%20bellig
Nesterov, A. (2005, May 21). Russia’s Attitude Toward the U.S.: Ally or Adversary? Retrieved from Worldpress.org: https://worldpress.org/Europe/2085.cfm
Pruitt, S. (2020, May 14). The Post World War II Boom: How America Got Into Gear. Retrieved from History.com: https://www.history.com/news/post-world-war-ii-boom-economy
Social Security Administration. (n.d.). Data Exhange Application. Retrieved from ssa.gov: https://www.ssa.gov/dataexchange/applications.html
Sun Tzu, e. a. (2016). The Art of War and Other Classics of Eastern Philosophy. Peter Norton.
Webster, I. (2021, December 25). CPI Inflation Calculator. Retrieved from http://www.in2013dollars.com: https://www.in2013dollars.com/us/inflation/1947


 Celebrating Memorial Day is not the right term to use for such a hallowed holiday. Being a veteran during the Cold War, I did not see battle, never drew a weapon to either defend or to defeat, and rarely saw death. However, there are three times in my career when I became inextricably linked to death of a fellow service member.
Celebrating Memorial Day is not the right term to use for such a hallowed holiday. Being a veteran during the Cold War, I did not see battle, never drew a weapon to either defend or to defeat, and rarely saw death. However, there are three times in my career when I became inextricably linked to death of a fellow service member.
 I want you to teach a person to drive a car using the following outline:
I want you to teach a person to drive a car using the following outline:

 I, as many others watched the recent presidential news conference, was somewhat surprised at some of the language that the President used in his monologue. I, at times, could not believe the tone and type of language that he used, but after some research looked for some Presidential language that could be better. However, I found the following quotes from a past US President. Can you identify who said this quote…
I, as many others watched the recent presidential news conference, was somewhat surprised at some of the language that the President used in his monologue. I, at times, could not believe the tone and type of language that he used, but after some research looked for some Presidential language that could be better. However, I found the following quotes from a past US President. Can you identify who said this quote…